🛡️ Enterprise Security Testing
Uncover Hidden Vulnerabilities Before Attackers Do
We deliver professional Vulnerability Assessment & Penetration Testing (VAPT) services that uncover security gaps, validate defensive measures, and provide clear, actionable strategies to strengthen and protect your organization.
Comprehensive Security Testing
nDepth Security:
Your Trusted Partner in Cybersecurity
At nDepth Security, we specialize in proactive defense
strategies to protect businesses from ever-evolving cyber threats. In this video, we discuss who we are, what we do, and how our expert team helps organizations strengthen their security posture.
From penetration testing and vulnerability assessments to managed security services and compliance consulting, we provide tailored solutions that safeguard your most valuable assets. Our mission is to go beyond identifying risks—we deliver actionable insights and cutting-edge security strategies to keep your business resilient.
Network & Infrastructure Testing
Deep analysis of your network architecture, identifying vulnerabilities in firewalls, routers, switches, and server configurations that automated tools might miss.

Web & Mobile Application Security
Comprehensive testing of web applications, APIs, and mobile apps using both automated scanning and manual testing techniques to uncover complex vulnerabilities.
Social Engineering Assessment
Assesses employee security awareness through targeted attempts to gain trust and manipulate individuals into revealing sensitive information or performing unauthorized actions. These tests help identify gaps in training and real-world readiness that may not surface in technical assessments.


Wireless Security Testing
Complete wireless network security assessment including Wi-Fi encryption, access point configuration, and rogue device detection.
Physical Security Assessment
On-site physical security testing, including access controls, surveillance systems, and facility security to identify potential physical attack vectors.


OSINT & Reconnaissance
We conduct Open Source Intelligence (OSINT) gathering to uncover exposed information and potential attack vectors that adversaries could exploit through publicly accessible sources.
Our Proven VAPT Process

Pre-Engagement Planning
Custom Rules of Engagement (RoE) tailored to your business needs, including testing strategy, schedule, and communication plan to ensure a worry-free experience.
Intelligence Gathering
Comprehensive reconnaissance using OSINT techniques to understand your attack surface and identify potential entry points that threat actors might exploit.

Vulnerability Assessment
Systematic identification and classification of vulnerabilities across your entire infrastructure using both automated tools and manual testing techniques.

Penetration Testing
Controlled exploitation of identified vulnerabilities to validate their impact and demonstrate real-world attack scenarios without disrupting business operations.

Analysis & Reporting
Detailed documentation of findings with risk ratings, business impact analysis, and actionable remediation recommendations prioritized by severity.
Remediation Support
Ongoing support to help implement security improvements and optional retesting to verify that vulnerabilities have been properly addressed.
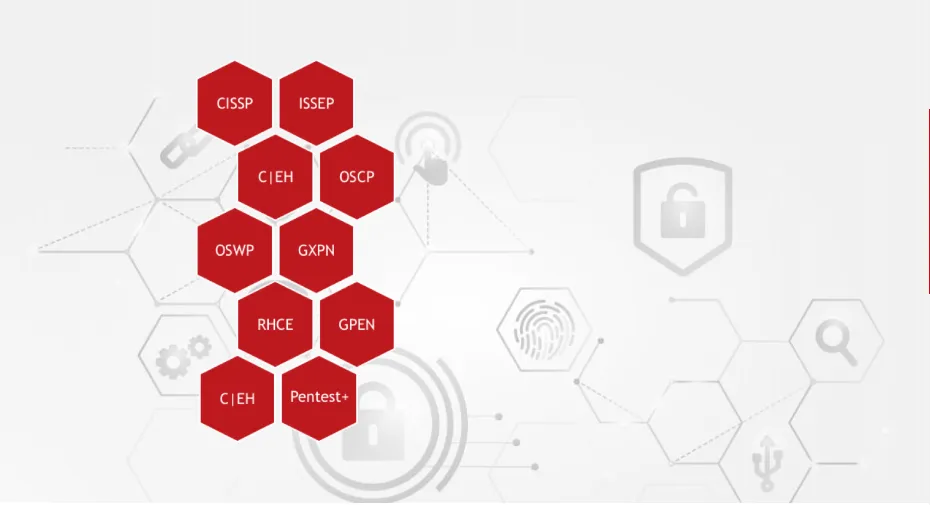
INDUSTRY CERTIFICATIONS
nDepth Security employs seasoned professionals with many industry-recognized college degrees and certifications: We strive to provide our customers with talented professionals that meet DoD 8570 education requirements (IAWIP).
ISC2, CompTIA, Offensive Security, GIAC, EC-Council,
etc.…
Industry Recognized
nDepth Security Wrote the Books on Penetration Testing
Nutting, Raymond (2018) CompTIA PenTest+ Certification (PT0-001) All-In-One Exam Guide, ISBN-10: 1260135942, New York, NY: McGraw-Hill Education.
Ammerman, Jonathan (2018) CompTIA PenTest+ (PT0-001) Practice Exams, ISBN-10: 1260440907, New York, NY: McGraw-Hill Education.
Nutting, Raymond & MacCormack, William (2020) GPEN GIAC Certified Penetration Tester All-in-One Exam Guide, ISBN-10: 1260456749, New York, NY: McGraw-Hill Education.
Nutting, Raymond & Ammerman, Jonathan (2019) CompTIA PenTest+ Certification Bundle (Exam PT0-001), ISBN-10: 1260454185, New York, NY: McGraw-Hill Education.
Ready to Secure Your Business?
Don't wait for a security breach to test your defenses. Our expert team is ready to conduct a comprehensive VAPT assessment that identifies vulnerabilities before attackers do.
Meet the Owners
Principles of nDepth Security

Raymond Nutting
(CISSP-ISSEP) brings over 23 years of battle-tested cybersecurity expertise to organizations that cannot afford to be vulnerable, from government agencies to healthcare systems to critical infrastructure. As co-founder of nDepth Security and holder of the industry's most respected certifications.

Cabral Mitchner
(CISSP) brings over 20 years of security engineering and assessment & authorization expertise, combined with a unique talent for building high-performing teams, fostering strategic connections, and creating win-win solutions that align security with business objectives. As Servant Leader and co-founder of nDepth Security, Cabral transforms both technical security challenges and human capital dynamics into sustainable frameworks.
STILL NOT SURE?
Frequently Asked Questions
We understand that Cyber Security may be confusing so here at 10 FAQS.
Question 1: "How do you customize your VAPT methodology to align with our industry, business risks, and compliance mandates (e.g., HIPAA, CMMC, FedRAMP)?
Every industry has unique regulatory frameworks, threat models, and compliance requirements. A cookie-cutter VAPT approach can overlook sector-specific risks or fail to meet mandatory audit standards. A provider that tailors testing to your environment ensures that findings are both relevant and actionable — safeguarding your compliance posture and reducing business risk.
Question 2: Do your testers hold advanced certifications like OSCP, CISSP, or GPEN — and are they actively keeping their skills current?
The cyber threat landscape evolves daily, and only professionals with hands-on expertise and current certifications can identify advanced attack vectors. A certified team — like nDepth’s experts with OSCP, CISSP, GPEN, and PenTest+ — demonstrates not only technical mastery but also a commitment to continuous learning, ensuring your tests are as realistic as possible.
Question 3: Can you simulate insider threats, supply chain attacks, and social engineering scenarios?
Not all threats come from external hackers. Insider threats, vendor compromises, and phishing/social engineering attacks often bypass traditional defenses. A VAPT provider that can replicate these advanced threat scenarios helps you uncover vulnerabilities that real attackers would exploit but that standard tests may miss.
Question 4: What is included in your final report, and will it be understandable for both technical and non-technical stakeholders?
A great report bridges the gap between engineering and executive teams. It should clearly explain risk impact, remediation priorities, and business implications, while also providing technical details for IT teams. A report that speaks to both audiences ensures vulnerabilities are addressed effectively and that leadership understands the ROI of remediation efforts.
Question 5: What frameworks and methodologies do you follow, and are you ISO/IEC 17020 accredited?
ISO/IEC 17020 accreditation sets a global benchmark for the competence and impartiality of inspection bodies — including VAPT providers. It validates that the provider’s testing processes, reporting, and quality controls meet rigorous international standards. When combined with recognized frameworks like PTES, OSSTMM, and NIST SP 800-115, ISO 17020 ensures your VAPT results are credible, audit-ready, and defensible during regulatory reviews. Choosing a provider without this level of accreditation may leave gaps in both trust and compliance assurance.
Question 6: Do you offer retesting after remediation — and is it included in your service?
Identifying vulnerabilities is only half the job; verifying they’re properly fixed is equally critical. Retesting ensures no issues linger, prevents recurring risks, and gives stakeholders confidence that security posture has improved. Providers that include retesting show commitment to outcomes, not just findings.
Question 7: Can your team test both cloud-native and on-premise environments, including SaaS, IaaS, and hybrid architectures?
Modern IT environments are often a mix of cloud services (AWS, Azure, GCP) and legacy systems. A provider that understands both cloud-native architectures and traditional on-prem environments can comprehensively assess misconfigurations, access controls, and vulnerabilities across the entire attack surface.
Question 8: How do you handle false positives and prioritize critical vulnerabilities?
A high volume of false positives or low-priority issues wastes time and resources. A skilled provider not only validates findings but also delivers a prioritized risk matrix, helping you focus remediation efforts on the vulnerabilities that pose the greatest business impact.
Question 9: How do you ensure minimal disruption to our operations during testing?
Poorly planned testing can cause outages, system slowdowns, or service interruptions. Professional providers like nDepth follow a Rules of Engagement (RoE) and Test Plan to ensure safety, proper timing, and minimal operational impact — all while maintaining realistic attack simulations.
Question 10: What kind of ongoing support or advisory services do you offer after the VAPT engagement?
VAPT is not a one-time checkbox. Threat landscapes evolve, and vulnerabilities reappear as environments change. Ongoing advisory services — such as remediation guidance, patch verification, and periodic re-assessments — ensure your organization remains secure and compliant long after the initial test.
INFORMATION ASSURANCE, TAILORED TO YOUR MISSION OR BUSINESS NEEDS.


@ 2025 nDepth Security LLC was founded in 2014 and is based out of Columbia, Maryland. nDepth Security LLC has proven operational skills, a keen sense of managing technology and has experience with leading and implementing critical functions within a diverse organization.






